Here are the steps for running HTTPS service locally for self-hosted wcf project. Please note that this is for test purpose only. Production environment requires SSL certificate installation & configuration on the related server.
- Make sure “makecert.exe” is available under: “C:\Program Files (x86)\Windows Kits\8.1\bin\x64”. Otherwise, please install Windows Kits first.
- Run Command Prompt in Administrator mode, navigate to the makecert.exe directory (“C:\Program Files (x86)\Windows Kits\8.1\bin\x64”) and type the command below for creating the authority certificate first:
makecert -sv SignRoot.pvk -cy authority -r signroot.cer -a sha1 -n "CN=EnderAuthority" -ss my -sr localmachineThe value of the “CN” key above is the name of the certificate authority.
- We need to move the authority certificate above to the trusted certificates for our PC by using the MMC(Microsoft Management Console). To do this, please press “Windows” button, type “Run”, hit enter and type “mmc” and hit enter once again.
- As given in the picture below, from the “File” tab, select “Add/Remove Snap-in” and select “Certificates”. Press “Add” button in the middle of the window, and select “Computer Account”. Hit “Next” and then hit “Finish”.
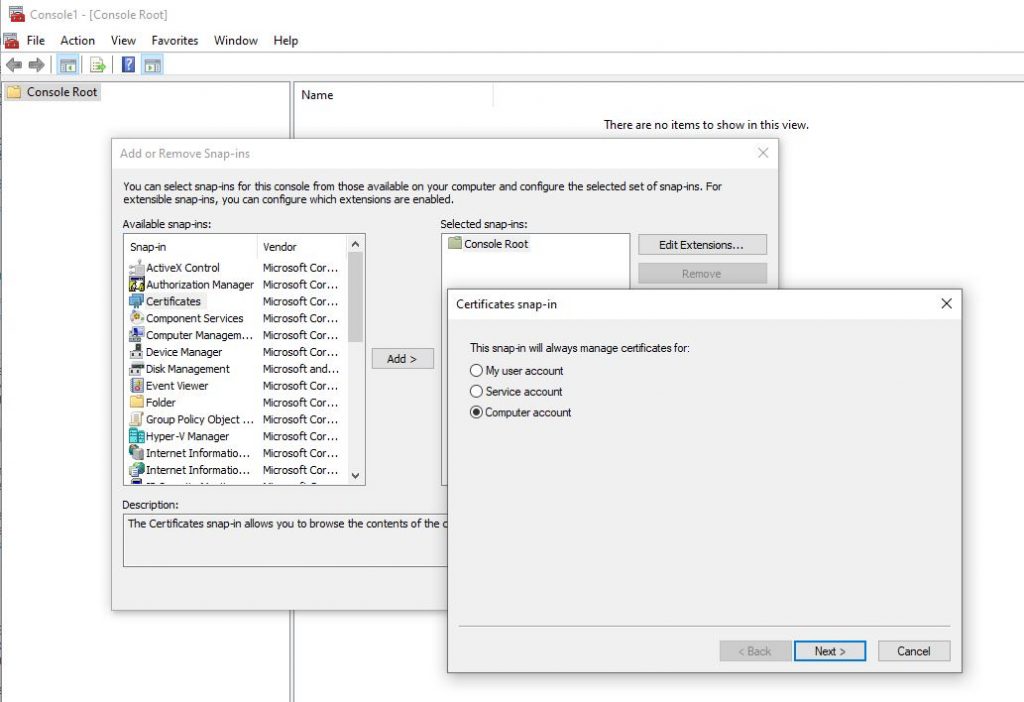
- In MMC, navigate to the “Certificates” – “Personal” – “Certificates” section and select your recently created certificate which has “Issued To” as CN name you’ve given in the above step (which is “EnderAuthority” for the example above). Once you select your sertificate, drag and drop it to the “Trusted Root Certification Authorities” – “Certificates” section.
- Now we are creating the actual certificate that we need by running Command Prompt in Administrator mode, navigate to the directory makecert.exe directory (“C:\Program Files (x86)\Windows Kits\8.1\bin\x64”) and type the command below:
makecert -iv SignRoot.pvk -ic signroot.cer -cy end -pe -n CN="10.0.0.29" -eku 1.3.6.1.5.5.7.3.1 -ss my -sr localmachine -sky exchange -sp "Microsoft RSA SChannel Cryptographic Provider" -sy 12- Since IP and port is required to link the certificate to your self-hosted WCF service, IP has been entered to the “CN” field of the command above.
- To link the certificate with our self-hosted WCF service, HttpConfig tool is required. Please download this application from the link below:
https://www.dropbox.com/s/r5ie9u9wzdhahs5/HttpConfig.zip?dl=0
- From the HTTPConfig’s SSL section please click on “Add”. In the SSL Configuration window, please fill the “IP Address” and “Port” of your service, and the “GUID” information that resides in your self-hosted WCF service’s solution folder – Properties – AssemblyInfo.cs – [assembly: Guid(….)] section.
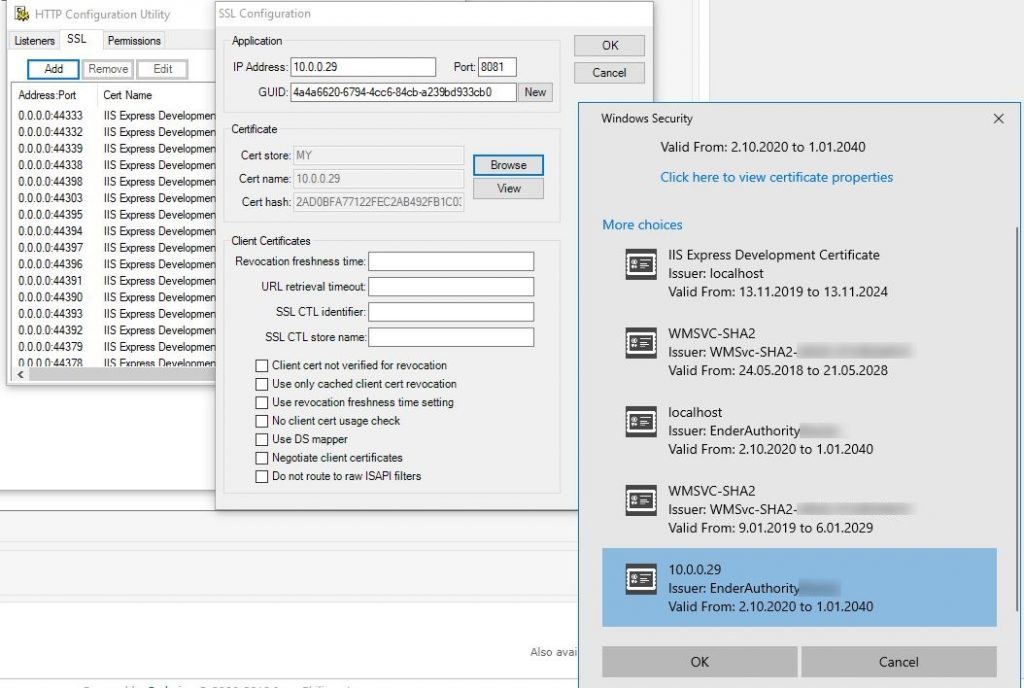
- Once you’ve completed relating your self-hosted service with the self-created certificate above, now you can focus on the App.config configuration in your self-hosted service solution:
<bindings>
<webHttpBinding>
<binding name="RestWebHttpBinding" maxBufferSize="2147483647" maxBufferPoolSize="2147483647" maxReceivedMessageSize="2147483647" transferMode="StreamedRequest" useDefaultWebProxy="true">
<readerQuotas maxDepth="32" maxStringContentLength="2147483647" maxArrayLength="2147483647" maxBytesPerRead="656000" maxNameTableCharCount="656000" />
<!-- Please uncomment below for enabling https -->
<!--<security mode="Transport">
<transport clientCredentialType="None"/>
</security>-->
</binding>
</webHttpBinding>
</bindings>
<behaviors>
<endpointBehaviors>
<behavior name="RestEndPointJson">
<webHttp defaultOutgoingResponseFormat="Json" helpEnabled="true" />
<crossOriginResourceSharingBehavior />
</behavior>
</endpointBehaviors>
<serviceBehaviors>
<behavior name="RestBehavior">
<serviceMetadata httpGetEnabled="true" httpsGetEnabled="true" />
<serviceDebug includeExceptionDetailInFaults="true" />
</behavior>
</serviceBehaviors>
</behaviors>
<service behaviorConfiguration="RestBehavior" name="Base35.Service.Implementation.SecuredChannelService">
<endpoint behaviorConfiguration="RestEndPointJson" binding="webHttpBinding" bindingConfiguration="RestWebHttpBinding" name="endpointjson" contract="Base35.Service.Interfaces.ISecuredChannelService" />
</service>Please include httpsGetEnabled=”true” to your behavior section.
In “webHttpBinding” section above, when “security” section uncommented, self-hosted service(s) can be used with https (please don’t forget to change the url from “http” to “https”).
By commenting out or uncommenting the “security” section of the “webHttpBinding” and using the “http” or “https” in the self-hosted service url, switch between http and https becomes possible.
- When necessary, please use the netsh commands given below to configure your http settings:
netsh http add urlacl url=https://+:54321/ user=ARGE-EYURDAKOC\EnderYurdakoc
netsh http delete urlacl url=https://+:54321/
netsh http show sslcert
netsh http show urlacl
That’s all 🙂
Resources:
https://www.codeproject.com/Articles/24027/SSL-with-Self-hosted-WCF-Service
https://www.codeproject.com/Articles/131048/WCF-self-hosted-service-over-HTTPS

Comments are closed.